Welcome to the Cyber Sizzler - the only cybersecurity newsletter that helps everyone from analysts to CEOs get 2% better every day.
We’re the Michael Scott of cyber newsletters, we laugh hardest at our own jokes and work non-stop to make everyone from CEOs to analysts 2% better every day.
ON DECK FOR TODAY
HEATING UP: Kremlin Burns and Dish is Served Cold
DUMPSTER FIRE: USSOCOM Takes Ethos a Little Too Seriously
CACHING IN: Gem Security has $11M Pink Diamond Hands 💎 🙌
JALA-MEME-ÑOS: 🌶️ 🤣
HEATING UP
Spicy opinions on things we care about for reasons
one /
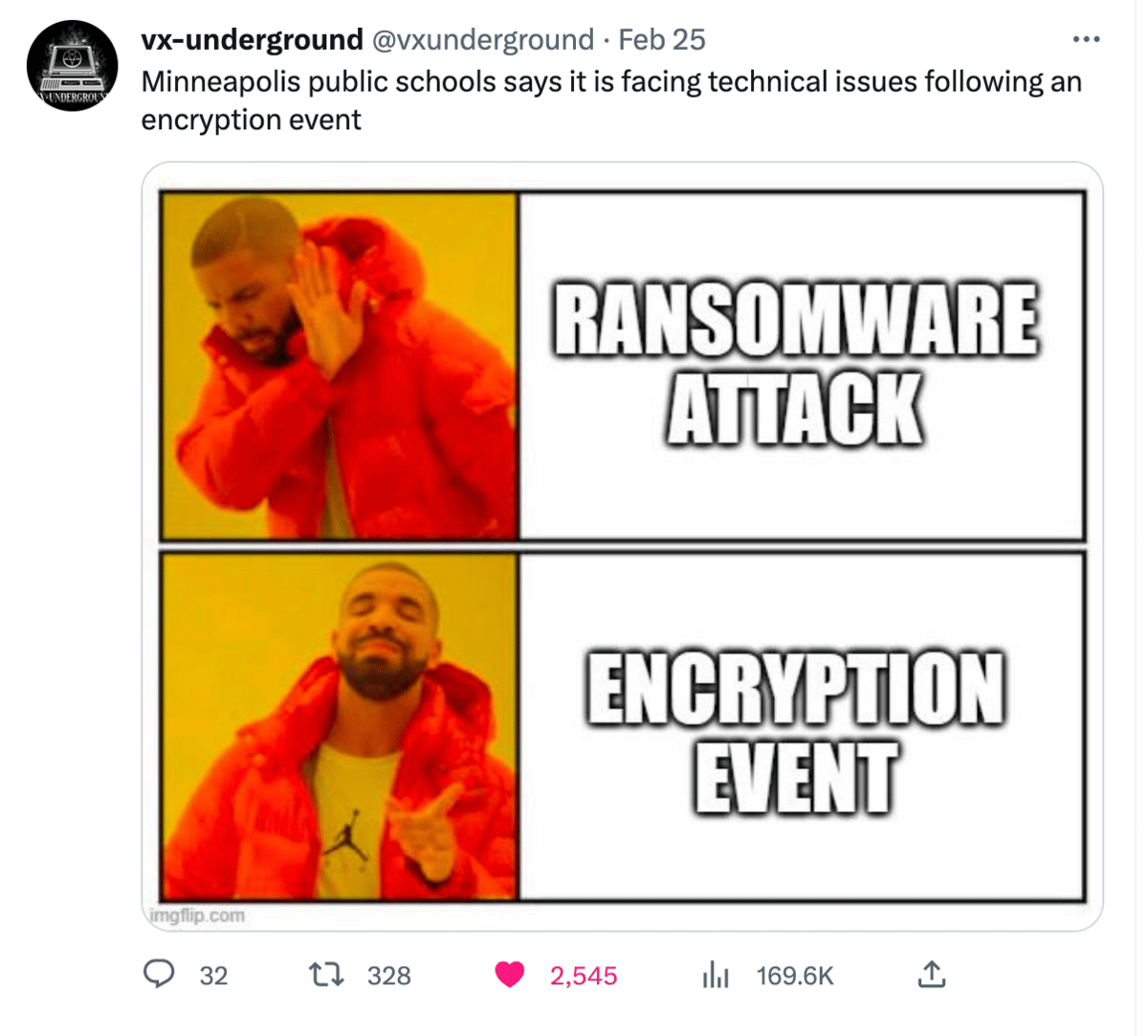
CH01 Lights the Kremlin on Fire
NKOTB hacked over 30 Kremlin run sites on Thursday 👏. We normally don’t cheer for compromises, but Russia (🖕) earns an exception.
Russia invaded Ukraine a year ago and the group CH01 has claimed responsibility. TechCrunch posted the following translated statement from the group.
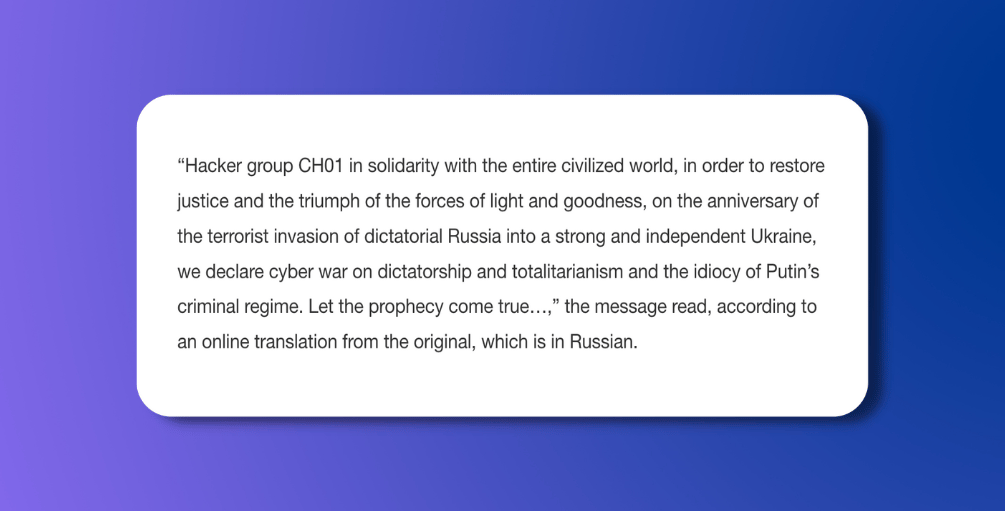
Again, we couldn’t agree more. Today we applaud the group, and will continue to do so as long as Russia continues its war against the sovereign nation of Ukraine.

two /
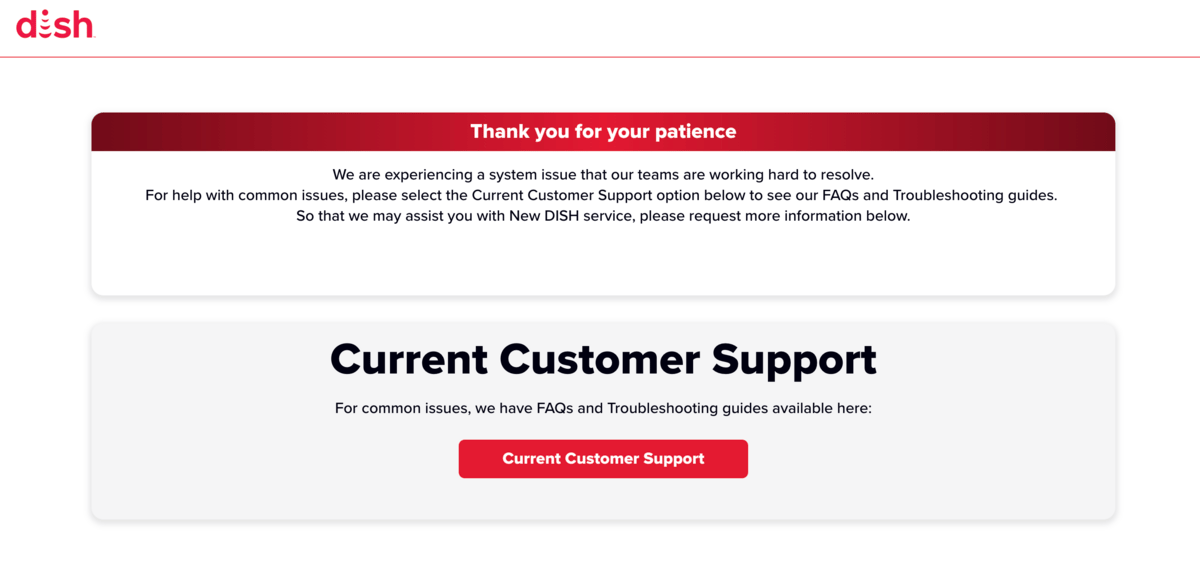
We Learned that Dish Network is Still in Business
Bleeping Computer reports that Dish Network is still a company, and one that’s under a cybersecurity attack. We literally didn’t realize that Dish was still a company, and a large one at that with Sling TV and Boost Mobile under its umbrella.
Nevertheless, hackers knew Dish Networks still existed and have proceeded to take down the company’s site. Still unfolding.
DUMPSTER FIRE
Eyebrow raising breaches that you already know about, but with our 🌶️ added

Affected: Unknown, but 70K are employed
Dwell time: 2 weeks (started on Feb 8, 2023)
Notification time: Feb 20, 2023
Identity monitoring: None 🙄 (we’re leaving this here, just because they’re the USG they don’t get a pass)
When we think of United States Special Operations Command (USSOCOM), we think of Jocko Willink. Hardcore badasses that do what they say they’re gonna do.
We didn’t realize that email systems were covered under the USSOCOM ethos “Humans are more important than hardware.”

But it appears to be the case because humans exposed the email storage device to the world without even basic protections like a password.
Security researcher, and all-around good guy, Anurag sen (twitter) played the cybersecurity version of the telephone game by alerting the folks at TechCrunch who alerted the USG. The server was secured shortly after.
We don’t know, and likely never will, if data was exfiltrated, but per gov’t rules none of the information would be classified at this time.
However, the USG has the habit of retroactively classifying data.
What’s that you ask?
Per Jonathan Abel, Fellow, Constitutional Law Center, Stanford Law School,
Retroactive classification means the government could hand you a document today and prosecute you tomorrow for not giving it back. Retroactive classification can even reach documents that are available in public libraries, on the Internet, or elsewhere in the public domain
What that means is the USG can classify documents at any point in the future. There will be a paper trail, none of this classification with your mind BS 🙄.
We’d love to know what happened.
If any of your USSOCOM buddies are peeling potatoes, can you ask them for us?

CACHING IN
We cover security start-ups that get money, security company mergers and acquisitions, and watch stock prices go up and down.
RAISED: $11M (seed)
DATE: February 1, 2023
LED BY: Team8
PARTICIPATED: Can’t find any
CEO: Arie Zilberstein
WHAT: Cloud sec
Our Take
Israeli startup Gem Security took in $11M from team8 at the beginning of the month. It’s a cloud-sec play in the early days of XDR.
We like the focus on TTPs, and multi-cloud, but want to see how this fits into the SOC. When the big dogs like SentinelOne play in a space (Singularity Cloud), you have to bring your A game.
It’s easy to understand what Gem does with their prominent CTA (call-to-action). Their website is sparse, but easy to navigate.
We know it’s the early days, but the content library needs work.
We’re not saying there’s nothing there, but if you took two articles away they’d have a Zero Day.
Gem Security is founded by Sygnia alums Arie Zilberstein & Ofir Brukner, and Singular alum Ron Konigsberg. Sygnia was another team8 backed company which was acquired in 2018. All were former Israeli Intelligence (Unit 8200)
Someone needs to tell these guys to get on Twitter; showcase what Gem can do. Plus, Twitter is where all the fun happens.
Hey Gem Security team , we’d love a demo 🌶️
Jala-meme-ños
🌶️ 🤣
TALL GLASS OF MILK
Time to cool down with a tall glass of milk. Thanks for reading! We'll be back tomorrow. In the meantime, feel free to reach out if you have any questions or feedback. Keep crushing it!
What'd you think of today's edition?
AFTERBURN
#bribery

If you made it this far could you help us out?
If you found this fun and interesting, could you share this with your team? We’re grassrootsing this thing and would love extra help spreading the word.
We don’t have challenge coins to give away (yet), but we’ll happily add you to our exclusive Cyber Sizzler Sweet Heat Database as a token of our appreciation.

It's like a secret club, but without the weird handshakes.
Simply share this email, reply to us and ask for access - done.